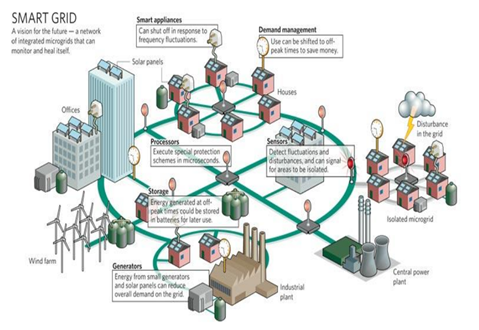
From 2GreenEnergy Intern Fabio Porcu: The Cyber Security of Smart Grids

Yet making a system of this type secure is non trivial, for two principal reasons:
- The number of networks and devices through which the data must pass is huge, each one of which may use different standards and protocols
- Each network can be accessed according to different safety standards, some of them are more rigid and others less, and this could allow the intrusion of hackers
Smart Grid introduces two-way communication for the first time, hence the need to protect the data that consumers and providers exchange; this did not happen in older networks because communication was one-way. A bi-directional communication is crucial in Smart Grid, and critically important insofar as it can contribute to ensure:
- Reduction of the load
- Management of consumption
- Storage of energy, for example, in electric vehicles
- Integration of renewable sources
The need for more refined data monitoring and intelligent measurement requires advanced control structure and security on the data transmitted. An attack or network failure could happen for several reasons:
- Breakage or failures of some component
- Hacking from a single point
- Hacking from several points of attack
A successful attack causes great inconvenience to customers in the affected area due to the interruption of electricity. To prevent the success of these attacks, the security strategy should be organized on several levels, so that even in the worst case where the attack is successful the damages are minimal.
More generally, the Smart Grid makes it possible to identify two different strategies for network security:
- Top-Down: analyzing the relative safety of the user scenarios and the automated meter reading and billing
- Bottom-Up: focusing on aspects of security as the device integrity, authentication, and approval from a device to join the network, manage key aspects, and detect intrusions.
Cyber threats on the Smart Grid can potentially represent a danger to national security, economic stability of the system and also to physical security. Power stations and the SCADA system (Supervisory Control and Data Acquisition) are most commonly targeted by hackers. Also the opening of energy networks to IP networks and protocols for data exchange introduces new elements of vulnerability.
Once a hacker finds an access point to the network and is able to enter, it becomes much easier to produce an attack cascading along the Smart Grid. For example, a hacker attack on the channel for the transmission of prices and consumption in real-time can allow thefts of energy or the remote control of appliances. Strict security systems, both hardware and software, are required to ensure the safety of the Smart Grid.
In addition to these aspects, we must also note the economic damage that can result; companies that provide the service are subject to millions of dollars of losses.
The Smart Grid should therefore:
- Prevent attacks
- Provide recovery procedures, i.e., mechanisms of survival or emergency management in case the attack is successful, so as to be able to limit damage and ensure minimum services considered indispensable are not interrupted.
One possible solution is a reset button on the encryption key in the smart metering when a piece of hardware needs intervention. Again, this is a hardware solution, where two more complex solutions can be:
- PKI (Public Key Infrastructure)
- IBE (Identity Based Encryption)
In particular, IBE can be very interesting for the Smart Grid because it is a system of distributed access without a previous configuration file. This allows an easy spread of low-power devices such as sensors, because they can send messages without the need to contact a server that manages access keys and user authentication. A perfect security system consists of hierarchical control levels including a central system and peripheral control systems.